Introduction
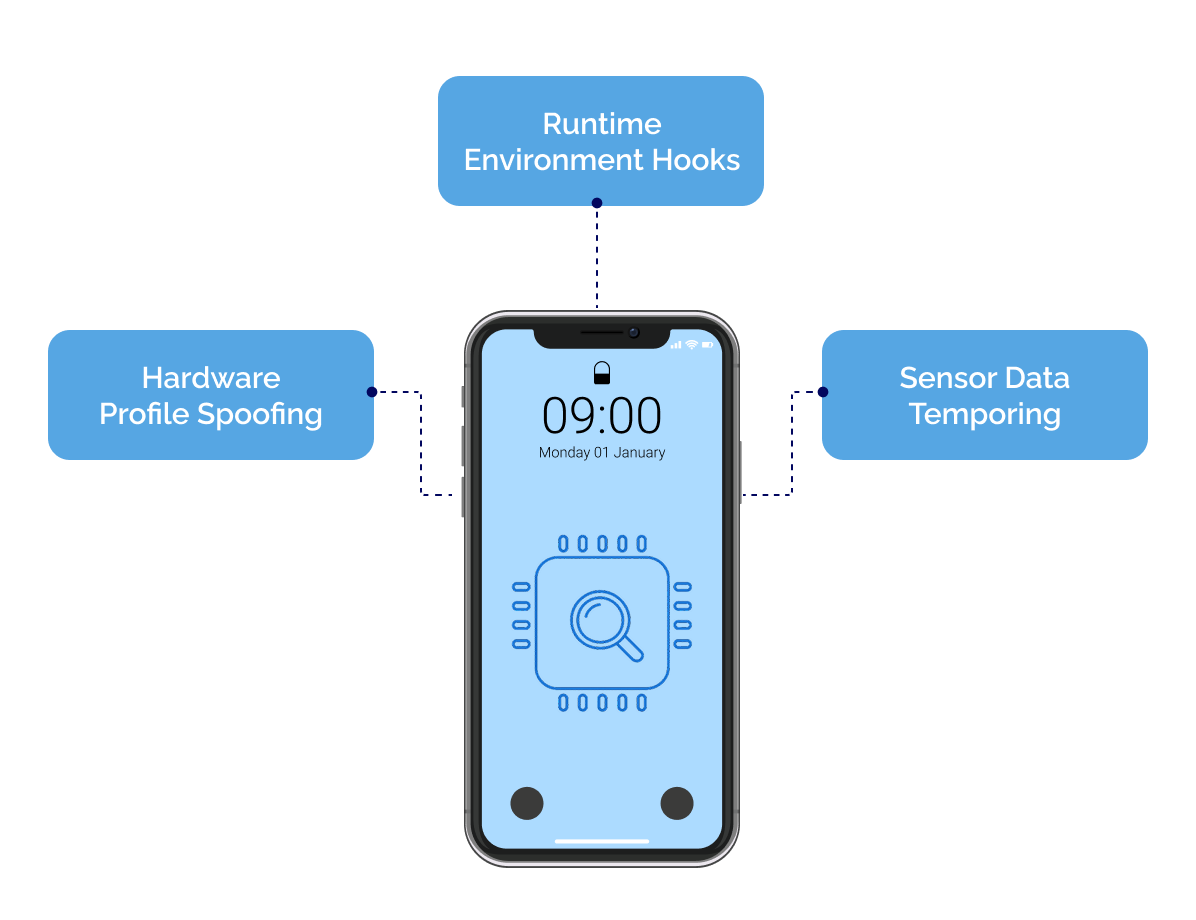
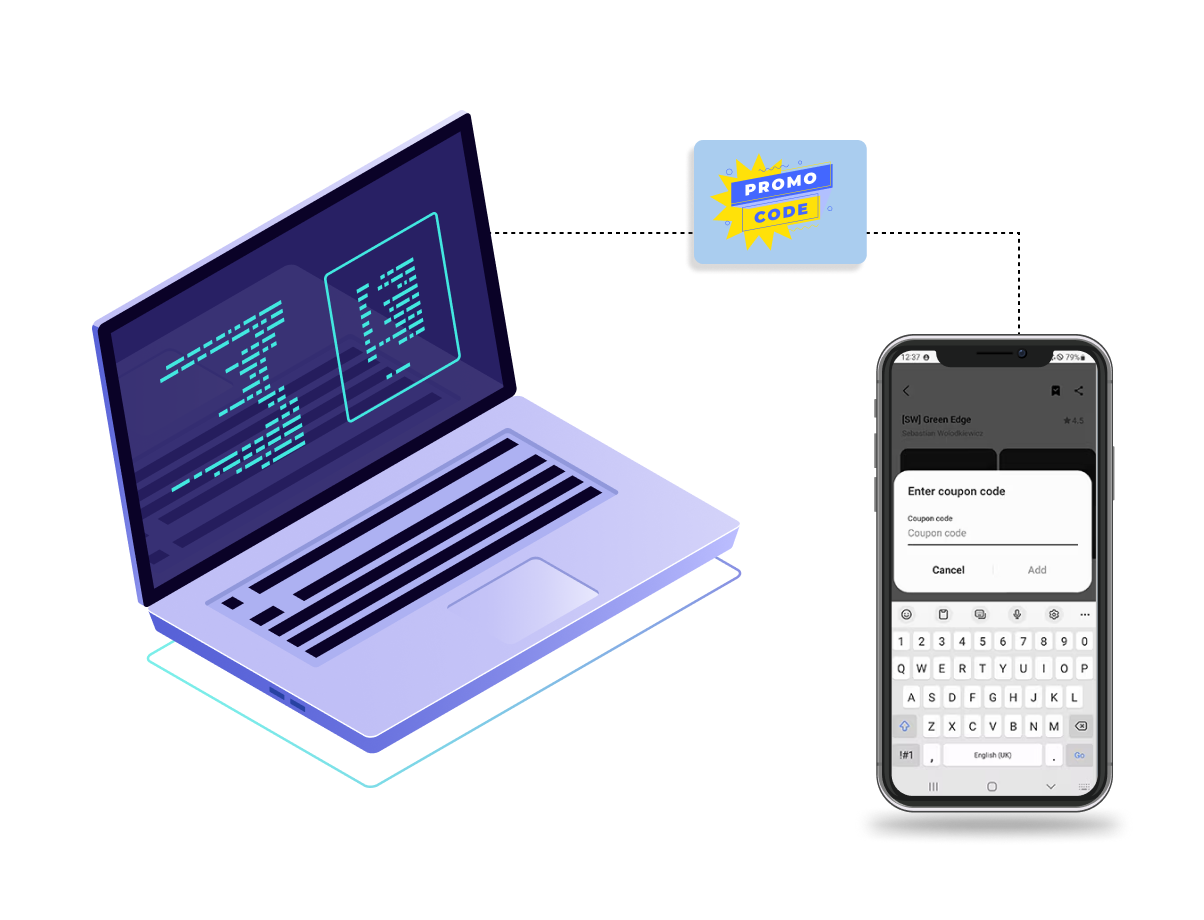
Fraudsters abuse promotions by manipulating or bypassing the promo code technically. Attackers are able to get multiple discounts on your app by switching browsers, using emulators, VPNs, or disposable emails for misuse.
DeepID uses device fingerprinting and intelligence to find such devices. It helps the company identify returning users, link multiple accounts created from the same account, detect emulators, and block or flag redemption in real time. It reduces the chances of coupon fraud and promo abuse.
Benefits for Businesses
- Continuous User Identification: DeepID detects users across sessions and accounts continuously.
- Accurate Account Linking: It uses device fingerprinting for device identification that helps businesses detect multiple account creations.
- Bypass Resistance Detection: This intelligence solution works against VPNs, emulators, and common spoofing methods.
Benefits of Promo Code Abuse Control
Plug and Play
The solution is straightforward and integration is effortless, We provide a simple and user-friendly interface.
Prevent Fraud
Prevent revenue loss caused by promo misuse from the fraudster with instant identification with DeepID’s promo code abuse control.
Accurate and Reliable
Prevent promo code abuse with accurate, reliable detection to stop misuse and protect your revenue effortlessly.
Blog
What is a rooted device? How to detect a rooted device?
What is Promo Code Abuse Control?
Why do businesses need this solution?
Can this solution detect multiple accounts on the same device?
Can Promo Code Abuse control identify emulator-based fraud?
Does it identify VPN and Proxy?
Does it work on Android and iOS?
Which industries will get the benefit from Promo Code Abuse Control?
Is there any solution for Coupon Fraud Prevention?
SIM Binding
Instantly check and confirm that only the legitimate user can access the app or service. A smart, seamless, and secure layer that links a user’s account to the registered SIM card.
Read More
Emulator Detection
Its emulator detection is designed to identify suspicious applications. It prevents automated abuse and fake user activity. It identifies the real device from emulators and helps businesses avoid losses.
Read More