According to statistics, nearly 60% of losses from digital transactions in India are linked to fraud rings. Digital onboarding is increasing, as are fraud networks taking aim at vulnerable KYC and device verification.
In this article, you will be able to learn more about the fraud rings in depth, the most commonly used tactics, as well as the best way to deal with the issue.
What is a Fraud Ring?
A Fraud Ring is used to define a group of criminals. The group collaborates on the resources to commit fraud, such as identity theft, credit card fraud, money laundering, and account takeover by sharing stolen information, techniques, tools, and methods to attack system weaknesses.
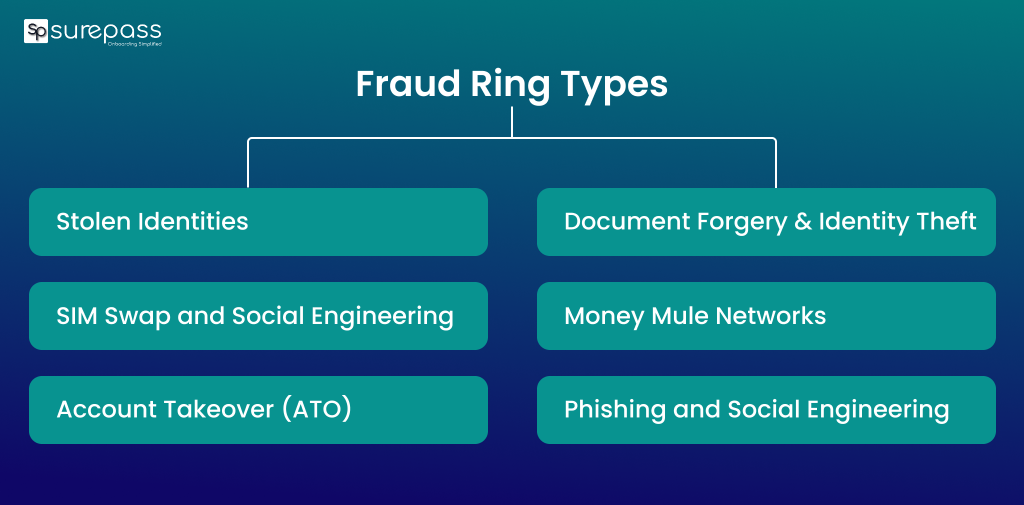
Fraud Ring Types
These are common types of fraud rings:
- Stolen Identities: Fraudsters steal personal data or use fake identities to open multiple accounts, obtain credit, or even pass KYC verifications. These identities can be used repeatedly across various platforms.
- Account Takeover (ATO): This fraud occurs when the user credentials are exposed due to a data breach. Fraudsters use this information to take control of legitimate accounts to carry out illegal transactions or create new accounts for fraudulent purposes.
- SIM Swap and Social Engineering: Fraudsters use social engineering to manipulate telecom companies or clients to transfer phone numbers to new SIMs. It helps in receiving OTPs, and also bypassing two-factor authentication.
- Document Forgery and Identity Theft: In this fraud, fake and manipulated documents are used to bypass identity checks, obtain a SIM, open accounts, or access financial services. These forged credentials are staples within organized fraud networks.
- Coordinated Multiple Accounts and Devices: Fraud rings create fake and duplicate accounts. These people use the same mobile, computer, internet connection, VPN, and emulators to show different people creating accounts.
- Money Mule Networks: Members of the ring, or recruited third parties, act as money mules. Passing illicit funds through their accounts to obscure the source and destination, monitoring, and law enforcement.
- Phishing and Social Engineering: These rings frequently use social engineering techniques to trick users into revealing credentials, OTPs, or personal information. This sensitive personal information can be used to commit illegal activities.
Automate your KYC Process & Reduce Fraud!
We have helped 3000+ companies in reducing Fraud by 95%
Industries Most Affected by Fraud Rings
The main target of this group is the company involved in transactions, onboarding, and digital payouts.
- Fintech and NBFCs: This fraud group creates fake accounts, uses fake or KYC documents, and misuses loan disbursal.
- Retail and E-commerce: Online shopping platforms face return fraud, misuse of stolen card details, and organized fraud where stolen products are resold for profit.
- Insurance: Fraud rings stage fake accidents, work with corrupt service providers, and inflate claims by showing exaggerated or unnecessary damage.
- Gaming and Betting Platforms: In Gaming and betting platforms, fraud rings exploit welcome bonuses and promotions through multi-accounting, emulator usage, and identity recycling.
- Telecom and Digital Lending Apps: SIM Misuse, identity fraud, OTP interception, and account takeovers are the common fraud tactics used to gain unauthorized access.

How Fraud Rings Impact Business Growth and Revenue
Fraud rings can affect a business in many different ways:
- Large Financial losses: This could cause fraudulent transactions, loan default, reward abuse, as well as unauthorized payments that directly affect revenues.
- Wrong User Growth Metrics: Fraud rings increase onboarding metrics with fake or mule accounts. This practice results in misleading analytics.
- Compliance Risk: Weak identity verification exposes businesses to regulatory scrutiny, penalties, and non-compliance with KYC and AML requirements.
- Chargebacks and Penalties: Increased fraud rates trigger chargebacks, platform penalties, and difficult relationships for banks and payment partners.
- Reputational Damage: Investigating and reducing fraud rings consumes internal resources and damages user trust.
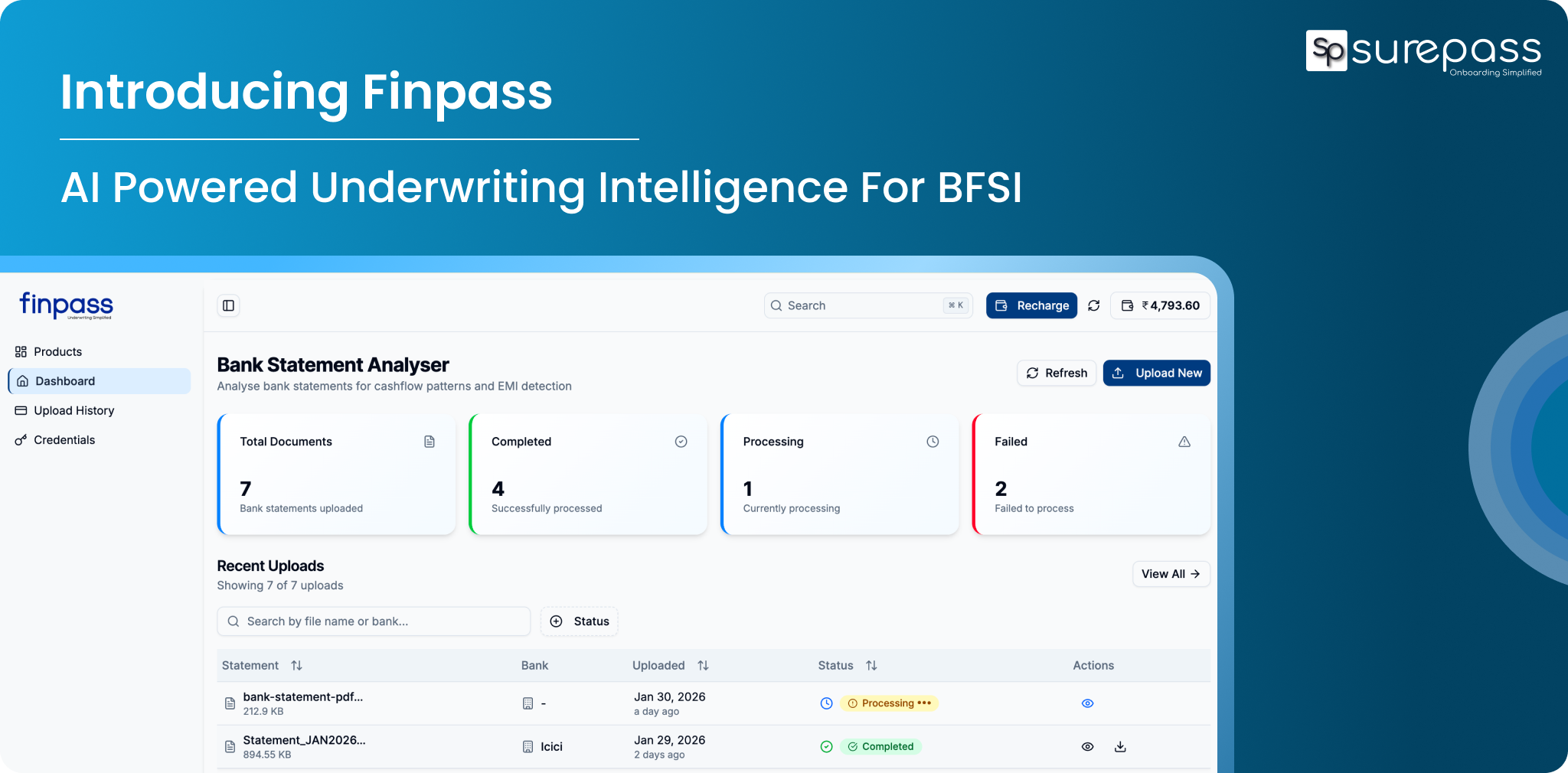
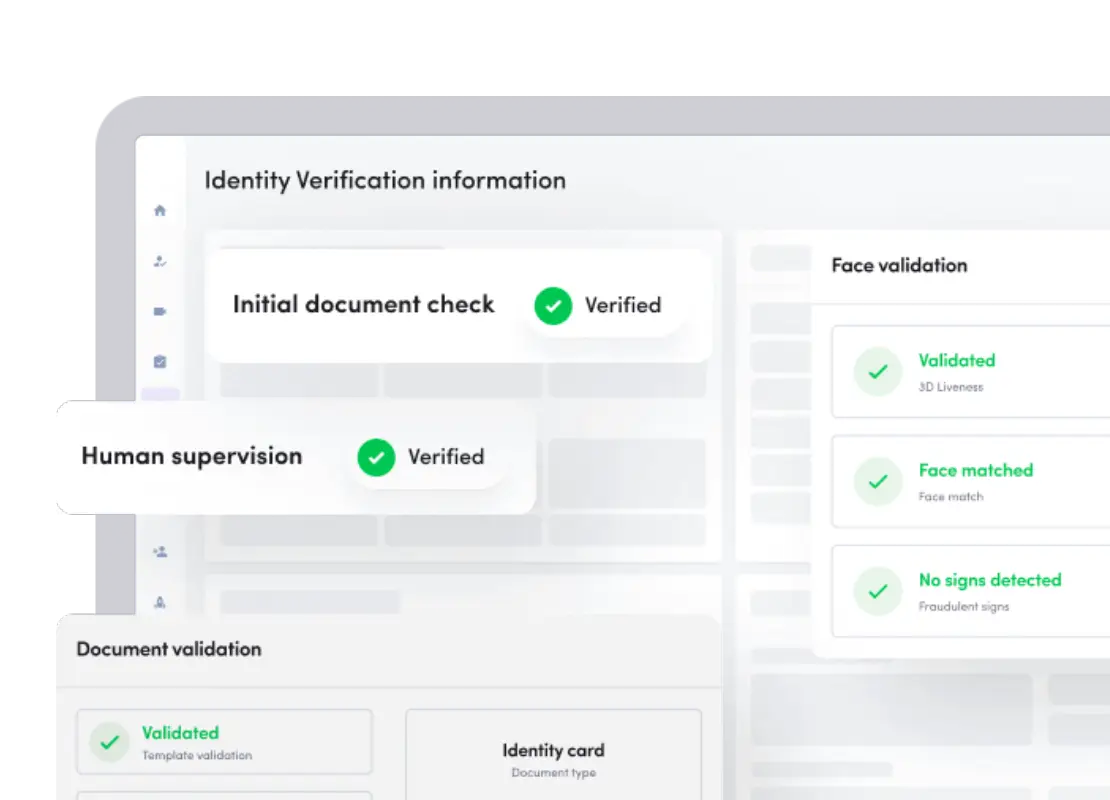
How Surepass Helps Businesses Detect Fraud Rings?
Surepass offers DeepID (mobile app security and device intelligence platforms) and verification solutions for fraud detection rings.
- Advanced Device Fingerprinting: DeepID gives a unique identifier to the device across sessions. It can detect the suspicious device even if the fraudster is using emulators, rooted phones, VPNs, or device spoofing techniques. It helps uncover multiple accounts linked to the same physical device.
- Emulator, Rooted and Tampered Device Detection: The DeepID device intelligence platform identifies the high-risk environments that fraudsters use to automate account creation and bypass app security.
- SIM and Mobile Intelligence: It detects SIM swapping, number recycling, and abnormal mobile usage patterns.
- Behaviour and Pattern Analysis: Fraud rings often follow repeatable patterns. The DeepID analyses login behaviour and onboarding velocity.
Conclusion
Fraud rings are a threat to businesses offering services online. These coordinated groups can impact businesses financially, damage reputation, and pose compliance risks. This makes it extremely important for businesses to use a security system for fraud ring detection. An easy-to-integrate SDK that identifies emulators, tools like FRIDA, SIM swapping, and rooted or tampered devices, helping businesses block such devices from accessing their services.
FAQs
Ques: What is a fraud ring?
Ans: A fraud ring is a group of criminals who commit illegal activities by exploiting system weaknesses.
Ques: What are the types of fraud rings?
Ans: Common fraud ring types include identity theft rings, phishing syndicates, account takeover (ATO) rings, document forgery networks, and money mule networks.
Ques: How can businesses identify a fraud ring?
Ans: Businesses can use a mobile app security solution to detect fraud rings.
Ques: What businesses are most affected by fraud rings?
Ans: The main targets of these rings include fintech, banking, gaming, e-commerce, telecom, and lending platforms.
Ques: Can fraud rings manipulate mobile devices?
Ans: Fraud rings use various tools such as emulators and rooted devices to bypass security checks and alter app behaviour.