Attackers use Frida to inspect, modify, and control Android apps even without changing the source code. Many attackers use Frida to hook it into Java and Native methods. It helps bypass security checks, modify app logic, and extract sensitive data in real-time. Such attacks pose a threat to Android app security and can be used to disable authentication, manipulate transactions, and reverse engineer business logic. To prevent such attacks, Android apps must detect Frida at runtime, because static protection alone is not enough.
What is Java-Based Frida Detection?
It is a security feature used in Android apps to identify whether Frida is hooking or manipulating the app at the Java runtime layer. It works under the Android Java layer, where app logic and security checks are written.
How Java-Based Frida Detection Works?
The Java-based detection focuses on finding signs of Frida inside the Java environment, such as:
- Suspicious or injected Java Classes and methods
- Runtime method hooking behaviour
- Debugger attachment or abnormal execution flow
- Unexpected changes in method responses
- Presence of Frida-related patterns
Automate your KYC Process & Reduce Fraud!
We have helped 3000+ companies in reducing Fraud by 95%
Where Java-Based Frida Detection is Used?
This Frida Detection method is used for various reasons:
- Protecting login and authentication logic:
It helps in finding runtime hooking attempts during login, OTP verification, or session validation. This reduces the credential bypass and unauthorized access.
- Detecting Runtime manipulation of business logic
It detects abnormal behaviour when attackers use Frida to manipulate Java methods. It includes payment validation and feature unlocking during app execution.
- Preventing Basic Reverse Engineering Attempts
It monitors the Java runtime that identifies suspicious hooks and debugging activity. It helps reduce the risk of reverse engineering and tampering.

Advantages and Limitations of Java-Based Frida Detection
Advantages of Java-Based Frida Detection
Easy Integration
It integrates easily with existing Java app code without the need for Android NDK or native development.
Quick Development
Developers can use and update the Java layer with minimal effect on app performance and user experience.
Effective Against Basic Attacks
Java-based Frida detection is effective for finding hooking and debugging attempts.
Limitations of Java-Based Frida Detection
Easy to Bypass
Skilled attackers easily bypass Java-based checks with advanced tools. These attackers can easily hook Frida for illicit purposes.
Unable to Detect Native Level Hooks
Java-based detection is ineffective against Frida activity happening in native (C/C++) code
- Limited Protection Against Advanced Reverse Engineering: It is not enough to provide defense against experienced attackers who use obfuscation bypass and native instrumentation.
- Not Sufficient for High Risk Apps: Apps dealing with financial transactions or sensitive data should not rely on Java-based detection.
What is Native Frida Detection?
Native Frida Detection is a security technique used in Android apps. It detects the presence of Frida at the native (C/C++) layer instead of Java level check. As Frida operates by injecting a dynamic instrumentation framework that hooks both Java and native code. It detects lower-level, making the app much harder to reverse engineer or tamper with.
How Native Frida Detection Works?
It is implemented using the Android NDK and focuses on identifying suspicious low level behaviour, such as:
- Detecting Frida server processes running on the device
- Monitoring suspicious threads and ports commonly used by Frida
- Using anti-debugging techniques like system call checks
- Scanning memory for Frida-related strings and signatures
Where is Native Frida Detection Used?
Native Frida detection is used for high security use cases, basically when Java-based attacks are not enough for identification.
- Protecting Critical App Logic at Native Level: Native Frida Detection helps in protecting critical operations implemented in native code, such as encryption, license validation, anti-fraud logic, and SDK protection. It prevents attackers from bypassing security by hooking native functions.
- Detecting Advanced Runtime Manipulation: Whenever the fraudsters try to alter native methods, memory, or system calls. The native Frida detection identifies abnormal behaviour and runtime tampering that cannot be detected at the Java level.
- Preventing Advanced Reverse Engineering: Native detection monitors low-level debugging, tracing, and instrumentation activity. It reduces the risk of reverse engineering by detecting tools that operate below the Java runtime.
Advantages and Limitations of Native Frida Detection
Advantages
- In-depth Inspection: Native code inspection allows for low-level checks of the app’s memory, file system, and running processes. It can be more thorough high-level checks.
- Detection of Advanced Techniques: Native checks can identify sophisticated instrumentation methods like Frida server, unusual system calls, or specific maps.
Limitations of Native Frida Detection
- Ongoing Arms Race: Modern attackers know the native detection methods. They use modified Frida Binaries that can easily bypass basic native checks.
- Complex Implementation: Native detection requires Android NDK Knowledge and native development expertise.
- Higher Development Effort: Implementation of native Frida detection is more complex than Java-based Frida detection.
- Regular Updates Required: The attack techniques evolve quickly, so native detection logic requires regular updates native detection logic.
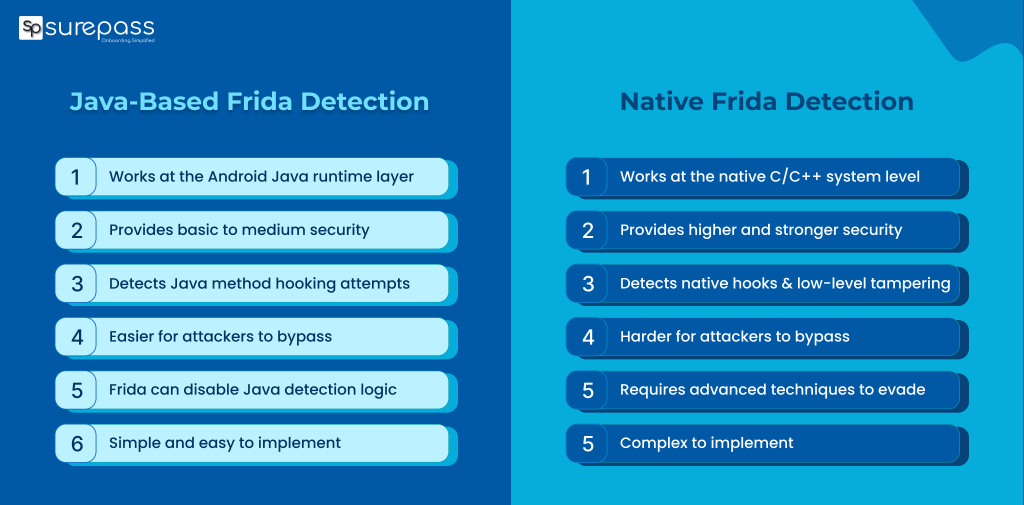
Java-Based vs Native Frida Detection: Key Differences
Java-based and Native Frida detection methods are used to protect Android apps from Frida attacks. However, both of them are different:
Strength Comparison
Java-Based Detection
- It works at the Android Java layer
- Offers basic to medium security
- Detects Java method hooking attempts caused by Frida instrumentation
- Good for apps requiring low to moderate security requirements
Native Frida Detection
- It works at the native (C/C++) system level.
- It offers more security than Java-based Frida detection.
Bypass Resistance Comparison
Java-Based Frida Detection
- Easier for attackers to bypass
- Frida can disable Java Detection logic
- Advanced attackers can hide Frida artifacts at runtime
Implementation Effort Comparison
Java Based Frida Detection
- It is easy to implement
- Do not require Android NDK
- Faster development and maintenance
- Cost effective
Native Frida detection
- It requires Android NDK and C/C++ expertise.
- More complex to develop and maintain
- Need testing over multiple CPU architectures
- Higher development effort
How to Secure an Android App from Frida Attacks?
Frida detection is essential for Android app security against runtime attacks, Java-based detection helps identify hooking attempts, and native detection protects logic and system interactions.
Businesses should use an advanced mobile app security solution that detects both to reduce the chances of security bypass and enhance protection from Frida attacks.
Conclusion
Both Java-based Frida Detection and Native Frida Detection are used to detect Frida attacks. However, at a deeper level, they are different parts. If we compare Java-based vs Native Frida Detection, then Java-based detection offers basic protection, and Native offers advanced protection. If the content contains sensitive personal or financial information, implementing native based detection is better, or the business can combine both methods for stronger security. In simple words, the hybrid approach will be best for Android App security.
FAQs
Ques: What is the Frida in Android App Security?
Ans: It is a dynamic instrumentation tool used to hook, modify, and analyze Android apps at runtime.
Ques: What is Java-Based Frida Detection?
Ans: Java-based Frida detection identifies Frida activity at the Android Java runtime layer.
Ques: What is native Frida Detection?
Ans: It identifies Frida activity at the C/C++ layer using Android NDK techniques.
Ques: What is better Java Based vs Native Frida Detection?
Ans: Both are good for Frida attack protection, depending on the use cases.
Ques: Does Native Frida detection require Android NDK?
Ans: No, it does not require Android NDK.
Ques: How to Secure an Android app from Frida Attacks?
Ans: Java and native detection, anti-debugging, and run-time monitoring should be used to secure Android Apps.