Introduction
In this blog, we’ll define the terms identification, verification, and authentication and explain what they mean in the context of online identities and cybersecurity.
Data breaches, compliance mandates, and identity theft have made it more difficult for businesses and individuals to build trust online. Yet, it is now more critical than ever for the same reasons.
There has never been a more pressing need to get it right, from the initial identification of a customer or user to the ongoing authentication process of ensuring that the person logging into or using your online services is the person you think they are. Identification, verification, and authentication all play a role in your ability to prevent fraud on your online channels, comply with KYC/AML and other identity-related regulations, and provide a positive customer experience.
What is Identification?
Identification is simply the process of a person claiming to be someone else. They can call themselves “Robert,” show a library card with their name, or have an email address with their name before the @ symbol.In the context of online transactions, users “identify” themselves by filling out a web form with their name, email address, or phone number, for example. Alternatively, when they buy a new pair of shoes online, they enter a credit card number and billing address. When using an identification process alone, as long as a person has the card holder’s information associated with a credit card or other form of identification, they are pretty much accepted.
A business that relies solely on identification is essentially admitting that they have no reason to doubt the person is who they claim to be, even though the information has not been independently verified as accurate. It’s the same as asking, “Who are you?” and accepting the answer at face value. For low-stakes transactions, such as purchasing a ticket to a sporting event or borrowing a book, having someone declare their identity without actually verifying it may suffice.
However, for most online transactions, identification alone is rarely sufficient. It’s the equivalent of having a username but no password.
So, how do we know that the person on the computer who is interacting with us is who they claim to be? This is where verification comes into play.
What is Verification?
Verification is more than just asking, “Who are you?” It then asks, “Are you really who you say you are?” and provides high confidence that the answer is correct.
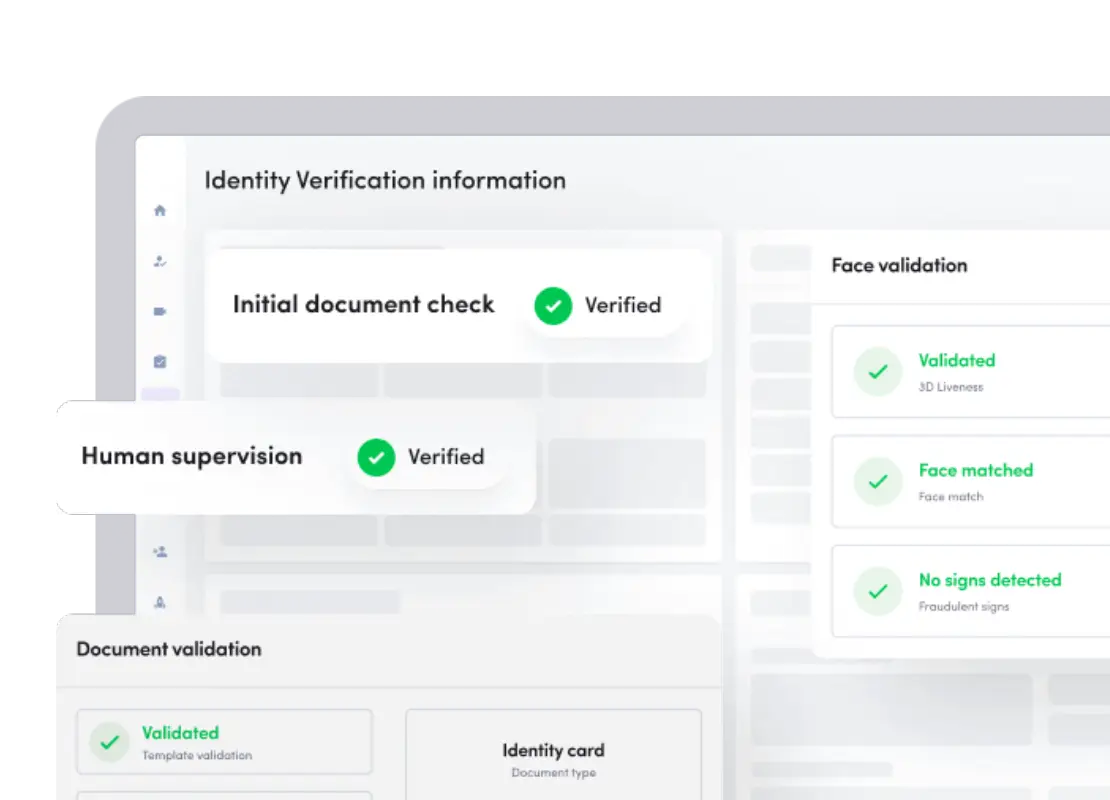
Establishing a trustworthy link between who someone claims to be and who they are necessitates the inclusion of an identity verification process in the onboarding or account opening process.
Typically, the verification process begins with verifying a government-issued ID document. Can we confirm the authenticity and validity of the documentation using document experts, advanced technologies, automated data extraction, and machine learning? Is there evidence of tampering?
Automate your KYC Process & reduce Frauds!
We have helped 200+ companies in reducing their user onboarding TAT by 95%
It takes time and effort to confirm someone’s identity with a high degree of certainty. Some service providers may cut corners and require a low barrier to entry to provide a “frictionless” onboarding process. For example, social media accounts typically only require new users to provide their name, email address, username, and password. For good measure, a phone number may be included as an identifier.
If a company has more stringent standards, it may rely on traditional identity verification methods, such as credit bureau searches or knowledge-based verification. The issue is that, as private information has become more prevalent on the dark web, that type of information has become less reliable. These organisations risk receiving information that leaves them unsure whether they’re dealing with a natural person or a fraudster.
Traditional verification methods do not meet the compliance mandates associated with these regulations, so businesses are beginning to shift to pairing a customer’s identity information with one of their biometric markers at the point of onboarding.
What is Authentication?
Verification is typically done only once, but once verified, one must authenticate a person’s identity each time they access a system or resource via an access control method.
You can “authenticate” someone simply by looking at them if you know them. However, because most transactions take place online or with people we don’t know, organisations implement systems to ensure that the person is who they say they are and not an impostor.
The user is asked to confirm that they are the same person who signed up for the service. Authenticating in low-stakes services may be as simple as having the user provide the password associated with a specific username or entering other specific login credentials.
- In traditional digital authentication, a person has certain pieces of information, or authenticators, in their possession, one or more of which has already been registered with the service provider at the point of signup or identity verification. You’ve probably seen two-factor authentication for an email account is a simple example of this.
- Most systems rely on one of three types of authenticators:
- Something the customer is aware of (e.g., security question, password)
- Something the customer possesses (for example, an ID badge, a cryptographic key, or driver’s licence)
- Something the customer is interested in (e.g., facial recognition, biometric data)
The number and quality of factors incorporated determine the strength of authentication systems — the higher the level and more factors used, the more robust the authentication system. For example, when logging into a social media account, you only need to provide a username and password (i.e., something you know). However, when you visit your local bank, you will be asked to show identification (i.e., something you have).
Unfortunately, because data breaches have made much of this private data widely available, the first two types of authentication – what you know or have – are no longer reliable.
The most secure systems demand proof of who you are via multi-factor authentication methods. In these cases, the service provider had already verified your claimed identity and paired it with a biometric when you signed up; they now compare that data to prove you provide at the time, such as a hand scan (if onsite) or a high-resolution selfie (if remote).
Surepass is at the forefront of this revolution. We work with some of the world’s largest corporations, assisting them in meeting compliance requirements, safeguarding their customers’ identities, and securing their business transactions. We’d be happy to tell you more about how we can assist your company in doing the same. Please get in touch with us at any time.